Is Bitcoin traceable? Coin security & privacy
Is Bitcoin traceable? Short, answer: yes. Long answer: It’s complicated. Here’s how to access privacy in crypto.

Table of Contents:
Privacy in crypto is an ongoing major theme, shaping innovations and driving discussions in the ecosystem. With this in mind, it’s only natural to wonder: is Bitcoin traceable, and to what degree?
The idea that Bitcoin and other cryptocurrencies are private is a fairly attractive narrative that has been sold to newcomers countlessly. After all, who would not want full control over their information and guaranteed coin security?
As enticing as the concept of default privacy in crypto sounds, it has (with exceptions) always been nothing but a common misconception, particularly on public blockchain networks, which represent the majority in the crypto space. Therefore, it is imperative to find a solution to interact with digital assets on the blockchain without giving away sensitive, personal information. It’s also worth noting that a sustainable privacy solution can only be achieved by taking back control over our privacy while remaining within the boundaries of legislation and compliance.
In this article, we will explore the concept of on-chain privacy, why most cryptocurrencies (with privacy coins being just the most obvious one out of several exceptions) are not private, and how this takes a toll on coin security. We will look into privacy coins and the validity of their claims towards creating private blockchains. Finally, we’ll explore the viability of achieving privacy in a cross-chain interoperable DeFi ecosystem while achieving regulatory compliance, answering at last whether can Bitcoin transactions can be traced or not.
Why blockchain anonymity is (for the most part) a myth
When Bitcoin emerged a decade ago, it promised an idea of pseudonymity and privacy. Naturally, people were excited about the ability to transact without giving up their personal information, unlike in traditional financial services.
At the time, few people noticed an inherent contradiction: On one side, the supposed pseudo-anonymity stood, and on the other, never-seen-before transparency was the major selling point of Bitcoin. It wasn’t long before a question began to surface: can Bitcoin be traced or not?
All Bitcoin blockchain transactions are recorded on an immutable ledger. No one can change the records afterward, nor could anyone conspire to alter the ledger. Yet, the Bitcoin blockchain has more than an unalterable bookkeeping function— it is completely public. Whereas banks can only reveal a statement to its account owner and maybe law enforcement, on the Bitcoin network, everyone can access all the information stored on the blockchain.
Taking this into consideration, “Are bitcoin transactions traceable?” is far from a binary question.
How do cryptocurrency transactions get traced?
Given a Bitcoin wallet address, you can check every transaction that ever involved it. Even without access to a wallet’s private key, users can still see a substantial amount of the financial information linked to that Bitcoin address. You can easily see how much Bitcoin it holds, and the same applies to other cryptocurrency transactions as well.
Although the faces behind the addresses are hidden, every transaction is public. And, while Bitcoin is often lauded as a way to transact completely anonymously, there are ways that a user’s real world identity can be revealed. For example, if someone's identity is linked to their Bitcoin address, any transactions they make, including illicit activities, can be traced back to them. This was exemplified by the recent arrest of the culprits of the 2016 Bitfinex hack, and the outcome of last year’s Colonial Pipeline hack, where authorities traced and retrieved part of a ransom payment.
Blockchain explorers are one of the most common ways to track Bitcoin and other cryptocurrencies. Blockchain explorers are tools that allow users to view and analyze blockchain data. Some cryptocurrencies like Ether (ETH) or Solana (SOL) have their own dedicated explorers.
While chain analysis is something anti-crime organizations perform to tackle criminal activities (ex: money laundering), there are also cases of users’ identities being tracked in the most mundane settings. A typical case occurs because virtual asset service providers (VASPs) like crypto exchanges are required to comply with know-your-customer (KYC) regulations. Any transaction in or out of a crypto exchange wallet leaves a clear trail connecting all self-custody wallets to their user’s identity. This opens a door for law enforcement agencies to subpoena the exchange for their KYC records and the user's digital asset transactions can be made transparent. On the other hand, newer techniques for purchasing bitcoins, have the potential to fully support anonymity and aid in crypto crime.
While Bitcoin promised a way to transact completely anonymously, it could only deliver pseudonymity. As such, it is possible to track Bitcoin and other crypto transactions through various means, including blockchain explorers, forensic analysis, and other methods. Individuals who wanted to keep their Bitcoin transactions anonymous searched for and developed methods to stay private, leading to the rise of Bitcoin mixers and coin tumblers. In essence, the transparent nature of Bitcoin made it impossible for anyone to use the network privately.
The myth of blockchain anonymity, or why Bitcoin IS traceable
Most cryptocurrencies and blockchain networks are open and transparent, for reasons that may surprise you. The founding idea behind Bitcoin, the mother of all digital currencies and blockchains, is decentralization. And the concept of decentralization has been thrown around in crypto-centric circles enough for many to not know what it means anymore.
Decentralization, in simple terms, means dissolving central authority and giving the right of governance to the stakeholders involved in the system, giving full control back to the ordinary user.
The idea of decentralization is quite familiar to how democracies work where instead of a single ruler making all the decisions, a government is mainly composed of an executive, legislative, and judiciary power keeping a check on each other. Similarly, decentralization takes the power from a single centralized authority and distributes it among all network participants keeping a check on each other.
Bitcoin is decentralized, as no company or group can lay claim to being decision-makers on the network. Unlike banks and governments, no one can freeze a person's access to the blockchain. However, this lack of a central authority poses a need for accountability of transactions since there are no governing bodies to verify them.
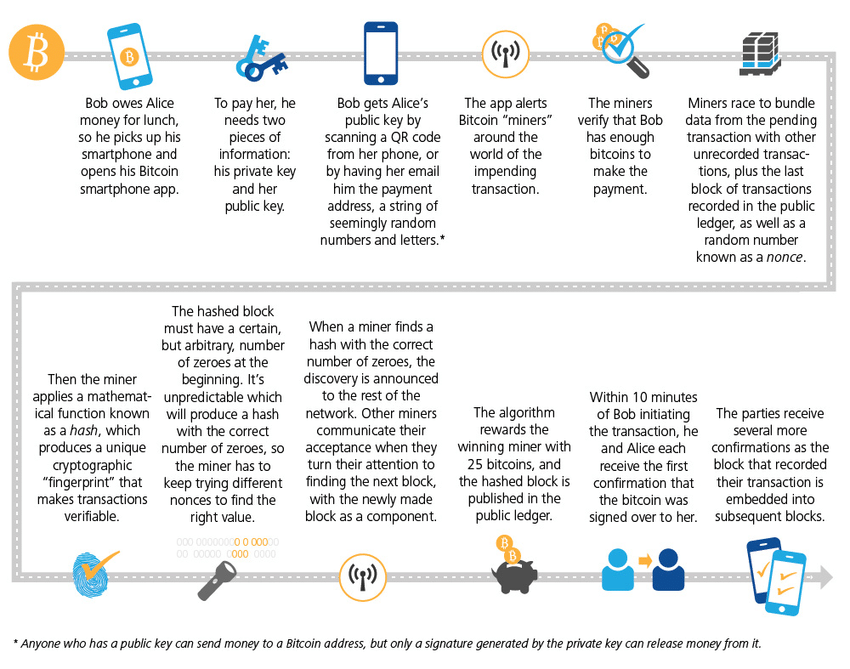
The Bitcoin network maintains its miners honest by issuing rewards to those that agree on an immutable network state. However, by design, miners alone shouldn't be trusted to verify transactions, as they’re likely to act in a way that maximizes their profit. Therefore, the network was made transparent and public so that anyone with access to the Internet could run a Bitcoin node and personally confirm if the miners' verification claims were true.
In this way, it wouldn’t be wrong to say that the radical transparency of public blockchains is both a feature and a bug. But doesn’t change the fact that It is secured with the same level of security employed by banks, the military, and virtual private networks (VPNs) to encrypt their systems: the 256-bit SHA hash algorithms. However, SHA hash functions provide each transaction a distinct fingerprint that cannot be reversed, unlike encryption, which can be decoded. Meaning that it grants your coin security.
Need for privacy coins
Privacy coins were born as a next step in the evolution of cryptocurrency.
Bitcoin’s creator(s) never had access to the technology necessary to make transactions that were fully private possible. Back in their days, the question “is Bitcoin traceable?” was too full of assumptions to be answered. Chain analysis tools were in too much of an early stage to swing users either way.
As soon as these standards were reached, new initiatives to restore true control over information to the average user and counterbalance the excess of transparency in the crypto space emerged. The earliest private blockchains such as Zcash were forked from the Bitcoin network. They adhered to the fundamental aspects of blockchain technology and the solutions that cryptocurrencies offered, but every similarity ended there.
Private blockchain networks didn’t take the path of open-ledger technology with all transactions open to the public along with receivers' and senders' addresses, amount of coins transferred, history of all transactions associated with addresses, etc. They, on the other hand, enabled users to conceal all these details.
Privacy-focused blockchains utilize privacy settings and advanced technologies like ring signatures, zero-knowledge proofs, and stealth addresses. Some of them have been largely successful at maintaining their users’ privacy. Zero-knowledge proofs, one of the most exciting technologies used in them, ensure that you can see that a transaction was successful but know nothing else about it –which, as you will learn, can have many applications.
Examples and comparison of privacy coins
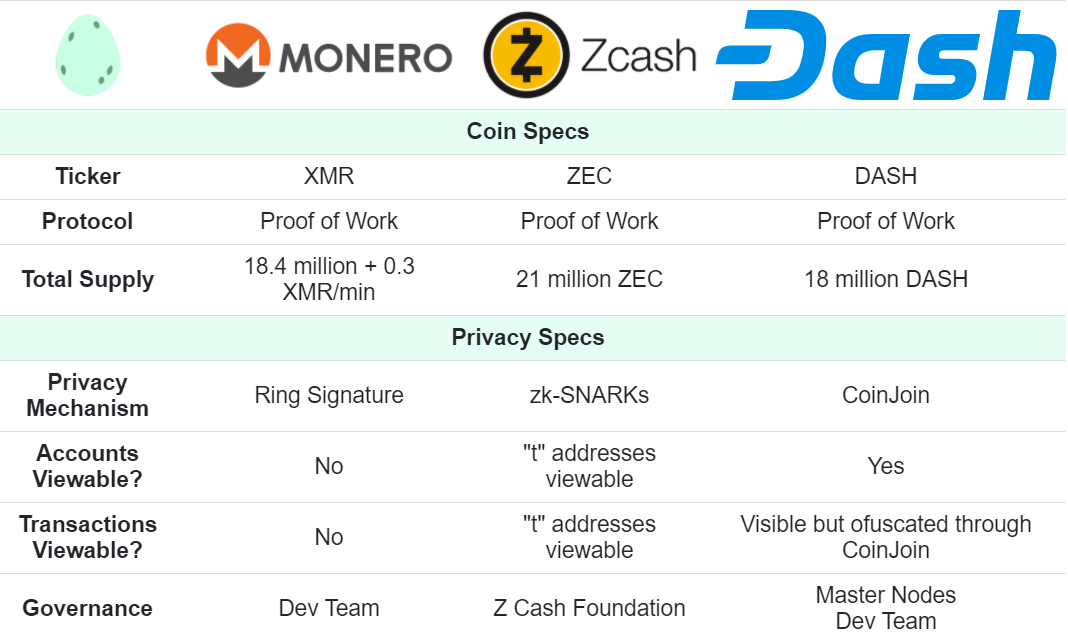
The most popular privacy coins include Monero (XMR), Zcash (ZEC), and Secret (SCRT). Other popular options are Beam, Grin, Verge, and Horizon (ZEN). These digital currencies use different technologies and cryptographic protocols to keep their users anonymous.
Out of all privacy coins, Monero and Zcash are the most well-known and have the highest market cap. Let’s have a look at these top two privacy coins and how they differ in terms of technology to enable privacy.
Monero
Monero (XMR) has made a name for itself in the crypto space as a leader in the private cryptocurrency space. The network uses ring signatures and stealth addresses to hide the identities of both parties in a transaction, as well as Ring Confidential Transactions (RingCT) to hide the amount involved in any transaction.
Unlike some of its competitors, Monero is a private-by-default blockchain. Although some groups have proclaimed to have cracked Monero's technology, most of those claims are largely disputed by the blockchain community.
Zcash
Forked from Bitcoin, Zcash famously claims to be “HTTPS if Bitcoin stands for HTTP”. Using advanced cryptography, Zcash allows its users to shield their transactions. Its zero-knowledge proof setup also facilitates shielded transactions, allowing users to send and receive coins without revealing their addresses to third parties.
Zcash’s ZK proofs also hide transaction amounts, adding an extra layer of privacy. Its technology is widely used in the crypto space today, adopted by many as a transparent way to access privacy. Like Monero, the network has been successful at keeping its users’ privacy.
Private but flawed: The drawbacks of private blockchains and privacy coins
Most privacy coins are true to their promise of anonymity, but it comes at a huge opportunity cost. In the past couple of years, the rise of decentralized financial services (DeFi) and Web3 has clouded the crypto space at large. Built on the ethos of cypherpunks and leveraging blockchain technology, the DeFi ecosystem offers almost all of the financial services seen in traditional finance, but without trusted third parties or middlemen.
But there's a caveat: the DeFi ecosystem at large is built on top of public blockchain networks. The same blockchain networks that antagonize private transactions or privacy in general. Privacy coins, on the other hand, offer top-notch privacy but lag behind in terms of DeFi innovations.
Furthermore, building a DeFi ecosystem on privacy coin networks would be like reinventing the wheel. Building a new DeFi ecosystem in silos rather than fixing privacy on existing DeFi carries along a range of complexities such as attracting new capital, training developers, fixing the same old scalability issues, etc.
The combination of complexities involved in building a new DeFi ecosystem, along with the composability issues in the existing DeFi ecosystem severely limits the prospects of private blockchains. This limits users’ privacy to mere simple wallet-A-to-wallet-B transactions, while missing out on financial services such as lending, borrowing, yield farming, stablecoins, decentralized cryptocurrency exchanges, and many more.
Regulatory compliance
Another major drawback of privacy coins is regulatory compliance. Even though privacy coins allow users to hide their sensitive information from public view, it then becomes tricky for them to prove they’re compliant, or to do so without disclosing all their information..
Solution offering privacy without achieving regulatory compliance will always end up in a tussle with regulators. This creates the need for a privacy solution that achieves regulatory compliance through voluntary, selective disclosures.
Panther Protocol: driving interchain privacy with compliance
The Panther Protocol prides itself as an end-to-end solution to privacy in Web3 and DeFi. The protocol also seeks to aid financial institutions as they aim for regulatory-compliant participation in decentralized finance. Panther combines the power of blockchain privacy with transparency, restoring trust in the system without sacrificing privacy.
Panther adopts zk-SNARKs cryptography, allowing users to perform shielded transactions across DeFi platforms with zero-knowledge proofs. Through a powerful multi-asset vault, the average cryptocurrency user can deposit their coins into Panther's vaults and mint a corresponding amount in zAssets (zero-knowledge, fully collateralized versions of the deposit). These zAssets support interoperability, allowing the user to move them across different blockchains and transact privately on public networks.
Panther protocol vs privacy coins
Panther's moat is in providing privacy in DeFi while allowing users to achieve compliance without sharing underlying data. Panther allows users to generate zero-knowledge reports to voluntarily disclose parts or their full transaction history with select counterparties.
Furthermore, Panther stands out from the crowd because it provides privacy across several blockchain networks. When users deposit digital assets into Panther, they break the on-chain link but continue to perform on-chain activities privately using Panther's zAssets.
Panther’s vision is to provide privacy features and power of choice to the entire DeFi ecosystem, in which users have complete control of their data and an ability to reveal as much or as little as they want, to whomever they want, at all times.
So, Is bitcoin traceable? Yes, very much.
Privacy on public blockchain networks is a myth, with the most popular cryptocurrencies only able to offer pseudonymity due to their transparency. Privacy coins have sprung up to fill the void, but their solutions do not make room for compliance or offer advanced financial services.
For a true solution to this dilemma, the crypto ecosystem needs to combine privacy, access to DeFi, selective transparency, and interoperability. Every attempt that fails to meet any of these requirements will either result in a siloed ecosystem, lack of public interest, or in further violations to users’ privacy. Private chains, even if they support smart contracts, are therefore not a solution to the need for privacy across the blockchain scene.
About Panther
Panther is a decentralized protocol that enables interoperable privacy in DeFi using zero-knowledge proofs.
Users can mint fully-collateralized, composable tokens called zAssets, which can be used to execute private, trusted DeFi transactions across multiple blockchains.
Panther helps investors protect their personal financial data and trading strategies, and provides financial institutions with a clear path to compliantly participate in DeFi.
Stay connected: Telegram | Twitter | LinkedIn | Website
